Creating a Secure AWS Cognito User Pool with AWS CloudFormation

Introduction :-
AWS Cognito is a robust service that provides user authentication and authorization for your web and mobile applications. When using Cognito, it’s essential to configure it properly through #AWS CloudFormation templates, which allow you to define and manage your infrastructure as code. In this example, we provide a basic CloudFormation template for setting up an #AWS Cognito User Pool, which is a fundamental component for managing user identities and authentication.
Here are the details for the simplified #AWS CloudFormation template for creating an AWS Cognito User Pool and its associated resources:
The
AWSTemplateFormatVersionspecifies the version of the CloudFormation template format being used, and theDescriptionprovides a brief description of the template's purpose.The
Resourcessection defines the AWS resources to be created. Here, we define a #Cognito User Pool named "MyUserPool" with the following properties:UsernameAttributes: Specifies the attributes that can be used as the username for sign-in. In this case, we've set it to "email."AutoVerifiedAttributes: Attributes that are automatically verified by Cognito. In this example, "email" is auto-verified.Policies: Sets a password policy for user passwords, requiring a minimum length of 8 characters and the inclusion of numbers.MfaConfiguration: Specifies the multi-factor authentication (MFA) configuration. In this case, it's set to "OFF," meaning MFA is not required.This section defines a Cognito User Pool Client associated with the User Pool created above. The client is named “MyUserPoolClient” and has the following properties:
UserPoolId: Refers to the User Pool resource created earlier, linking the User Pool and the User Pool Client.GenerateSecret: Determines whether a client secret is generated for this client (false in this example).ExplicitAuthFlows: Specifies the authentication flows supported by the client. In this case, "ALLOW_USER_SRP_AUTH" is allowed, indicating Secure Remote Password (SRP) authentication.SupportedIdentityProviders: Indicates that Cognito is the identity provider for this client.The
Outputssection defines output values that can be used to reference the created resources. In this case, it provides the IDs of the Cognito User Pool and User Pool Client for reference in other parts of your AWS infrastructure.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the #AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the #AWS CloudFormation service from the AWS Management Console.
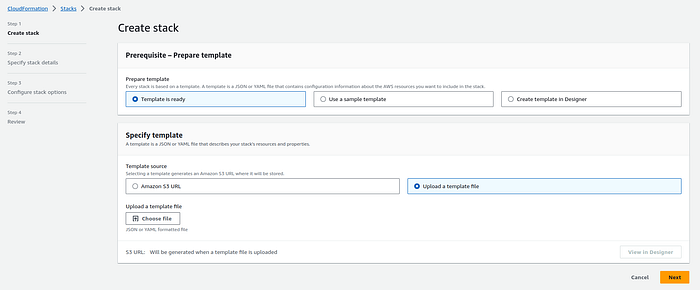
3. Click the “Create stack” button.
4. Upload the #CloudFormation template file (YAML).
Yaml:
AWSTemplateFormatVersion: '2010-09-09'
Description: AWS CloudFormation Template for an AWS Cognito User Pool
Resources:
UserPool:
Type: AWS::Cognito::UserPool
Properties:
UserPoolName: MyUserPool
UsernameAttributes:
- email
AutoVerifiedAttributes:
- email
Policies:
PasswordPolicy:
MinimumLength: 8
RequireNumbers: true
MfaConfiguration: OFF
UserPoolClient:
Type: AWS::Cognito::UserPoolClient
Properties:
UserPoolId: !Ref UserPool
ClientName: MyUserPoolClient
GenerateSecret: false
ExplicitAuthFlows:
- ALLOW_USER_SRP_AUTH
SupportedIdentityProviders:
- COGNITO
Outputs:
UserPoolId:
Description: ID of the created Cognito User Pool
Value: !Ref UserPool
UserPoolClientId:
Description: ID of the created Cognito User Pool Client
Value: !Ref UserPoolClient
5. Specify Stack Details:
Enter a #Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The #CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion
In this #AWS CloudFormation template, we’ve demonstrated a simplified configuration for an #AWS Cognito User Pool and User Pool Client. This template sets up the essential components, including the user pool’s name, username attributes, password policy, and multi-factor authentication settings. While this template provides a starting point for your authentication needs, it’s essential to note that #Cognito offers more advanced features like #Lambda triggers, custom email configurations, and social identity providers, which can be #integrated as required.
