Revolutionize Your Infrastructure: Implementing Detect Scan on Terraform Modules via CircleCI

Overview :-
Infrastructure as Code (IaC) security is becoming increasingly important in modern development practices. By implementing detect scan functionality for Terraform modules through CircleCI, teams can identify potential security issues early in their development cycle.
Setting Up the Environment
To begin implementing detect scan on your Terraform modules, you’ll need:
A Github Repository to implement the detect scan on terraform modules.
A CircleCI account connected to your repository
Terraform modules in your codebase
Basic understanding of YAML configuration
Step 1: Configure Terraform Modules
Create a directory with name detect_scan and within the directory create one more directory named terraform_modules and add some terraform code into it “for eg., click here and copy the terraform code from our existing Blog”. or you can use your own Terraform code if exists.
Ensure that your terraform_modules(directory) are structured properly and contain all the necessary files, such as
.tffiles, variables, and providers.
Step 2: Configure CircleCI
open the detect_scan directory using a code editor such as VS code.
create a folder named .circleci in the detect_scan directory. within the .circleci folder create a circleci configuration file named config.yml like this
.circleci/config.yml. This file defines the jobs, workflows, and steps for CircleCI.Define a new job in the configuration file to run the Detect scan on your Terraform modules.
provide the ./path to your terraform modules. As shown in the below job.
version: 2.1
jobs:
detect-scan:
docker:
- image: circleci/python:3.9
working_directory: /tmp/workspace
environment:
ENV_FILE: /tmp/workspace/
DOCKER_BUILDKIT: "1"
BUILDKIT_PROGRESS: plain
steps:
- checkout
- attach_workspace:
at: /tmp/workspace
- run:
name: Install detect-scan
command: |
pip install detect-secrets
- run:
name: Run detect-scan
command: |
detect-secrets scan ./terraform_modules/ --all-files
workflows:
version: 2
detect-secrets:
jobs:
- detect-scan
Step 3: Triggering the Detect Scan
Commit and push your changes to the GitHub repository.
CircleCI will automatically detect the changes and trigger a build based on the configuration defined in
.circleci/config.yml.CircleCI will execute the Detect Secret scan job defined in the configuration file.
Detect Scan will scan the specified Terraform module if any secrets were being hardcoded in your terraform code
you can see the detect-scan job running in the below figure.
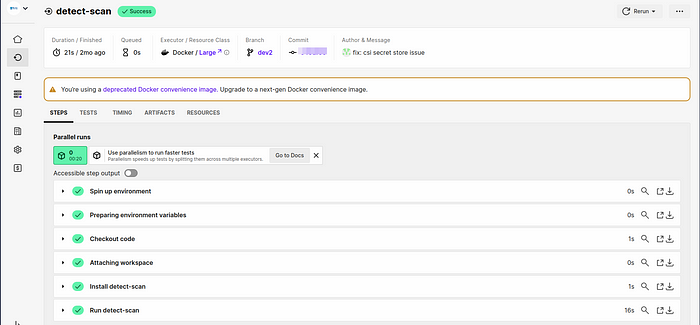
Step 4: Review the Detect Scan Results
Once the CircleCI job is complete, navigate to the CircleCI dashboard or the specific build/job in your browser.
Locate the detect scan step within the build logs or artifacts.
you can find the result in the last step of the detect scan as shown below.
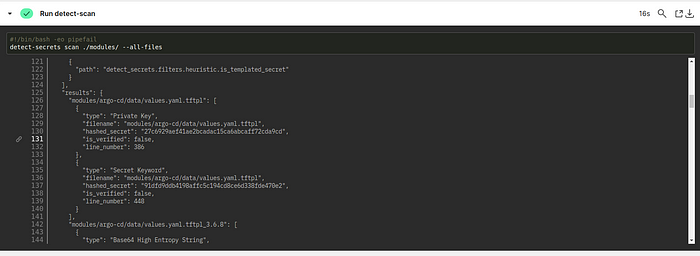
Conclusion :-
Implementing detect scan on Terraform modules through CircleCI helps teams maintain secure infrastructure code. Regular scanning, combined with proper configuration and monitoring, creates a robust security framework for your IaC implementation.
