
Photo by Stephen Phillips - Hostreviews.co.uk on Unsplash
Streamlining AWS Compliance: A Guide to Email Notifications for Non-Compliant Resources
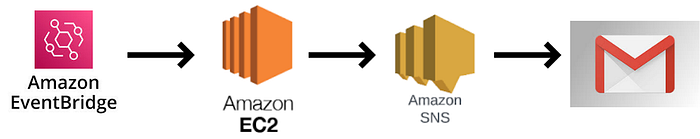
Overview :-
In the ever-evolving landscape of cloud governance, ensuring AWS resource compliance is paramount. AWS Config provides a robust solution, and in this guide, we’ll delve into the essential process of setting up email notifications for non-compliant resources. By leveraging this feature, you fortify your cloud infrastructure’s integrity, promptly addressing any deviations from established best practices.
Pre-requestites :-
- An AWS Account with proper permissions.
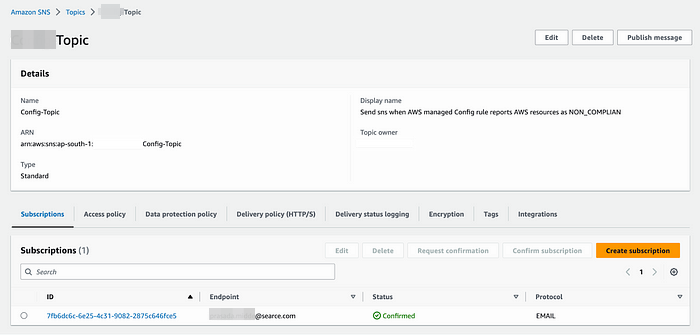
Step-1 :- Create SNS Topic :-
Login to your Aws account and navigate to sns service.
Create a Sns topic and Subscription with protocol as Email.
Create CloudWatch EventBridge Rule :-
Navigate the Cloud Watch and Cick on EventBridge.
Choose Create rule: Rule
Name, enter a name for your rule. If needed, enter a Description as well.
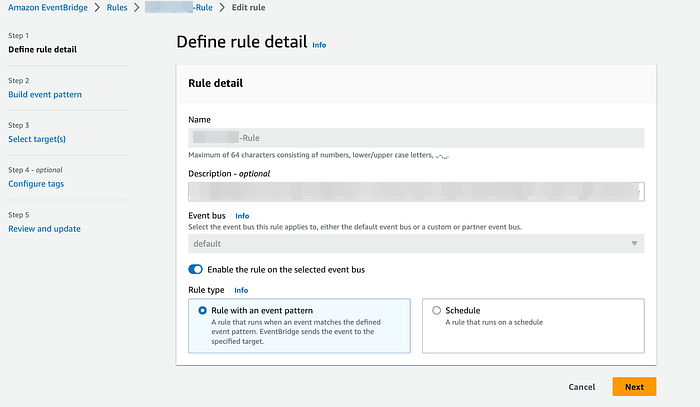
4. For Rule type, choose Rule with an event pattern. Then, choose Next.
5. For Event source, choose AWS events or EventBridge partner events.
6. In the Event pattern pane, choose Custom patterns (JSON editor), and then copy and paste the following example event pattern:
{
"source": [
"aws.config"
],
"detail-type": [
"Config Rules Compliance Change"
],
"detail": {
"messageType": [
"ComplianceChangeNotification"
],
"configRuleName": [
"EC2_VOLUME_INUSE_CHECK",
"ENCRYPTED_VOLUMES"
],
"resourceType": [
"AWS::EC2::Volume"
],
"newEvaluationResult": {
"complianceType": [
"NON_COMPLIANT"
]
}
}
}
7. Choose Next.
8. For Target types, select AWS service.
9. For Select a target, choose SNS topic.
10. For Topic, choose the SNS topic created in step-1.
11. Expand Additional settings. Then, for Configure target input, choose Input transformer.
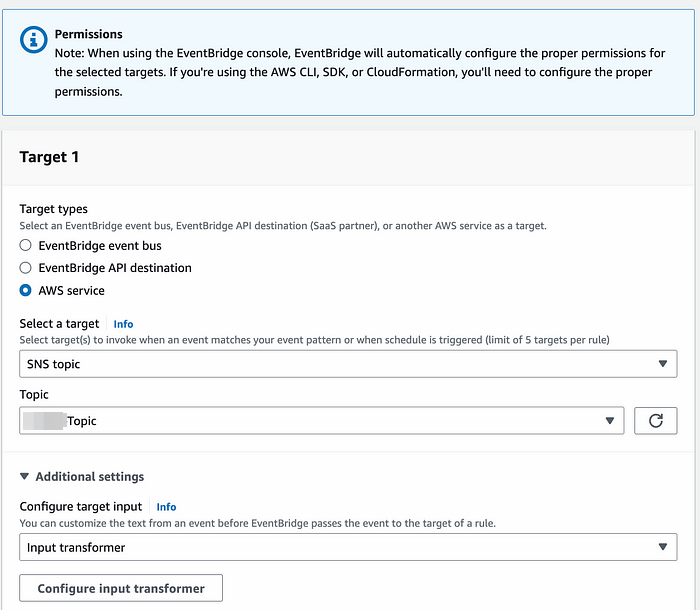
12. Choose Configure input transformer. Under Target input transformer, for the Input Path text box, copy and paste the following example path:
{
"awsRegion": "$.detail.awsRegion",
"resourceId": "$.detail.resourceId",
"awsAccountId": "$.detail.awsAccountId",
"compliance": "$.detail.newEvaluationResult.complianceType",
"rule": "$.detail.configRuleName",
"time": "$.detail.newEvaluationResult.resultRecordedTime",
"resourceType": "$.detail.resourceType"
}
13. In the Template text box, copy and paste the following example template. Enter the time, rule, resource type, resource ID, AWS account ID and AWS Region, compliance, and resource information as required by your use case.
"On <time> AWS Config rule <rule> evaluated the <resourceType> with Id <resourceId> in the account <awsAccountId> region <awsRegion> as <compliance> For more details open the AWS Config console at https://console.aws.amazon.com/config/home?region=<awsRegion>#/timeline/<resourceType>/<resourceId>/configuration"
14. Choose Confirm. Then, choose Next.
15. Optionally, you can Add new tag. Then, choose Next.
16. Choose Create rule.
17. After an event type is triggered, you receive an SNS email notification with the custom fields populated from step 13 similar to the following:
"On ExampleTime AWS Config rule ExampleRuleName evaluated the ExampleResourceType with Id ExampleResource_ID in the account ExampleAccount_Id in Region ExampleRegion as ExamplecomplianceType. For more details open the AWS Config console at https://console.aws.amazon.com/config/home?region=ExampleRegion#/timeline/ExampleResourceType/ExampleResource_ID/configuration"
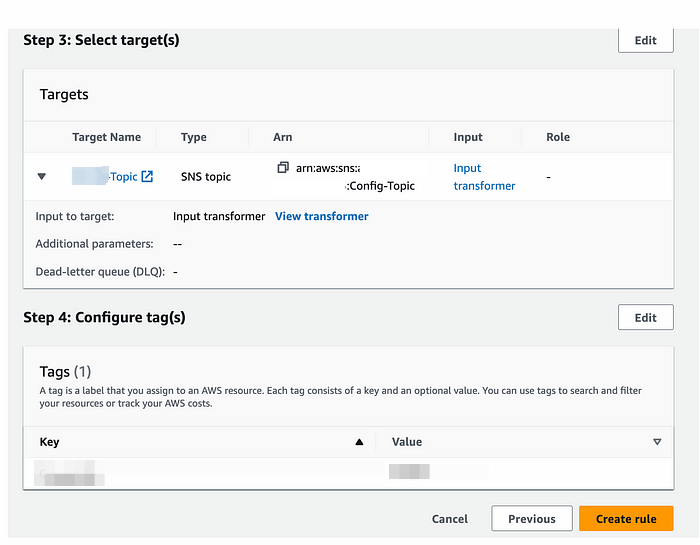
Create AWS Config Rule :-
Go to the AWS console and Naviagte to Config service
Click on create Rule
If you not enabled the AWS Config before please follow the below link to enable it
Setting Up AWS Config with the Console
Set up AWS Config to use Amazon SNS to notify you of configuration changes and Amazon S3 to store history and snapshot…
4. Select Add AWS managed rule
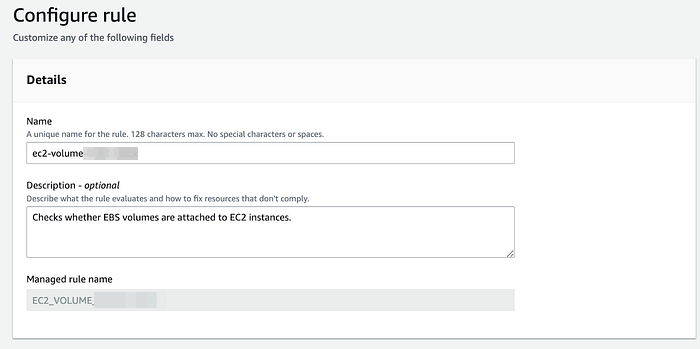
5. Select the Rule here that i have selected : ec2-volume-inuse-check (to get the unattached volumes or available volumes ) and click on Next
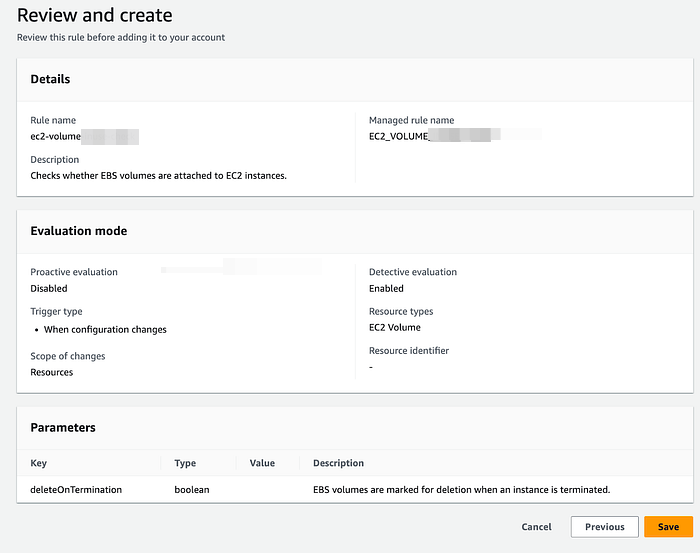
6. Provide Name and Description of the Rule and leave rest of the options as default and click on Save to create a Rule.
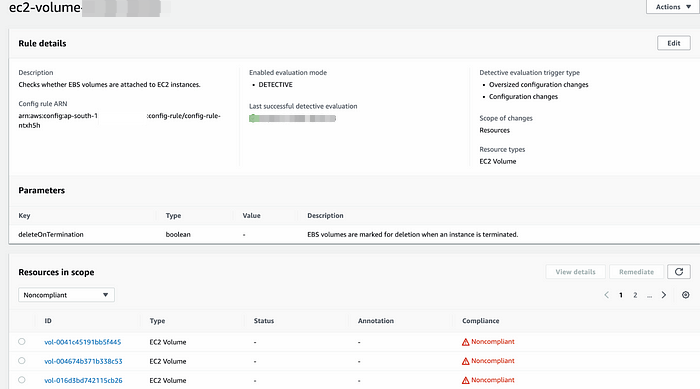
7. Once the rule created then it starts evaluating the resources (EBS Volumes) and after few minutes click on the rule, Under Resource in scope it will display the Noncompliant resources.
8. The Amazon EventBridge Rule detect these changes in the Rule and it triggers the SNS notification via email and you will receive the emails to your subscribed email.
9. You will get sample email like below and if you note down the VolumeID and cross verify that in the console and you can see that the Volume is in Available state.
Conclusion :-
Achieving and maintaining AWS resource compliance is more than a regulatory requirement; it’s a cornerstone of a resilient and secure cloud infrastructure. By implementing email notifications for non-compliant resources, you’ve elevated your organization’s ability to respond promptly to any deviations. Stay vigilant, stay compliant, and navigate the AWS cloud with confidence. Here’s to a secure and compliant cloud journey! 🚀✉️ #AWS #Compliance #CloudSecurity #AWSConfig #CloudGovernance
