Transform Your Terraform Security Game with This CheckOV Implementation Hack using Circleci

Introduction :-
Hey there! Let’s talk about something that’s really helpful when working with Terraform — implementing CheckOV in your CircleCI pipeline. If you’ve been wondering how to make your infrastructure code more secure and compliant, you’re in the right place. I’ve been using this setup for a while now, and I’m excited to share how it works.
CheckOV helps us scan Terraform code for security and compliance issues. Think of it as having a friendly security expert looking over your shoulder while you code. What I really like about this tool is how it catches potential problems before they become actual problems in production.
Pre-requisites :-
Before we dive in, let’s make sure you have everything you need:
A CircleCI account connected to your repository
Basic knowledge of Terraform
A GitHub repository with your Terraform modules
Git installed on your system.
Step 1: Configure Terraform Modules
Create a directory with name checkov and within the directory create one more directory named terraform_modules and add some terraform code into it “for eg., click here and copy the terraform code from our existing Blog”. or you can use your own Terraform code if exists.
Ensure that your terraform_modules(directory) are structured properly and contain all the necessary files, such as
.tffiles, variables, and providers.
Step 2: Configure CircleCI
Go the checkov directory.
create a folder named .circleci & within that folder create a circleci configuration file named config.yml like this
.circleci/config.yml. This file defines the jobs, workflows, and steps for CircleCI.Define a new job in the configuration file to run the Checkov on your Terraform modules.
provide the ./path to your terraform modules. As shown in the below job.
Here’s a simple .circleci/config.yml file to get you started.
version: 2.1
jobs:
checkov:
docker:
- image: bridgecrew/checkov:latest
working_directory: /tmp/workspace
environment:
ENV_FILE: /tmp/workspace/
DOCKER_BUILDKIT: "1"
BUILDKIT_PROGRESS: plain
steps:
- checkout
- attach_workspace:
at: /tmp/workspace
- run:
name: Install checkov
command: |
pip install -U checkov
- run:
name: Run Checkov
command: |
checkov --directory ./terraform_modules/ > checkov_output.txt
# Upload the output file to CircleCI artifacts
- store_artifacts:
path: checkov_output.txt
destination: checkov_output
workflows:
version: 2
checkov:
jobs:
- checkov
Step 3: Running CheckOV on your terraform modules using circleci
Commit and push your changes to the GitHub repository.
CircleCI will automatically detect the changes and trigger a build based on the configuration defined in
.circleci/config.yml.CircleCI will execute the Checkov job defined in the configuration file.
Checkov will scan the specified Terraform module if any mis-configurations were being present in your terraform code
you can see the checkov job running in the below figure.
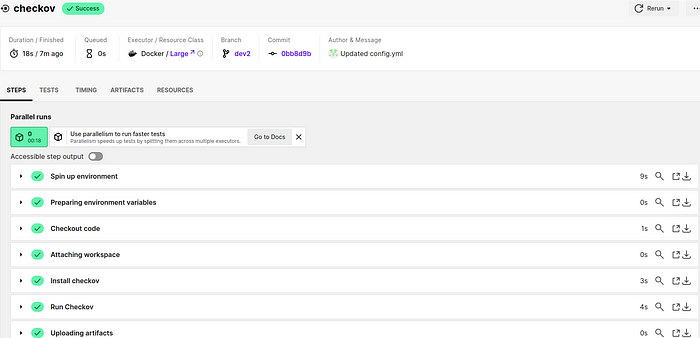
Step 4: Review the checkov Results
Once the CircleCI job is complete, navigate to the CircleCI dashboard or the specific build/job in your browser.
Locate the checkov step within the build logs or artifacts.
you can find the result in the Artifacts of the checkov job as shown below.
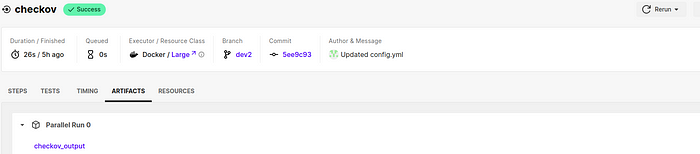
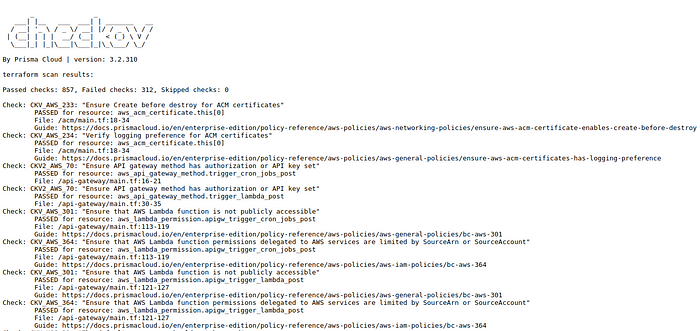
Conclusion :-
Setting up CheckOV with CircleCI isn’t just about adding another tool to your pipeline — it’s about building better, more secure infrastructure from the start. I’ve found that this combination helps catch issues early and saves a lot of time in the long run.
Remember to regularly update your CheckOV version to get the latest security checks. And don’t forget to customize the rules based on your specific needs.
