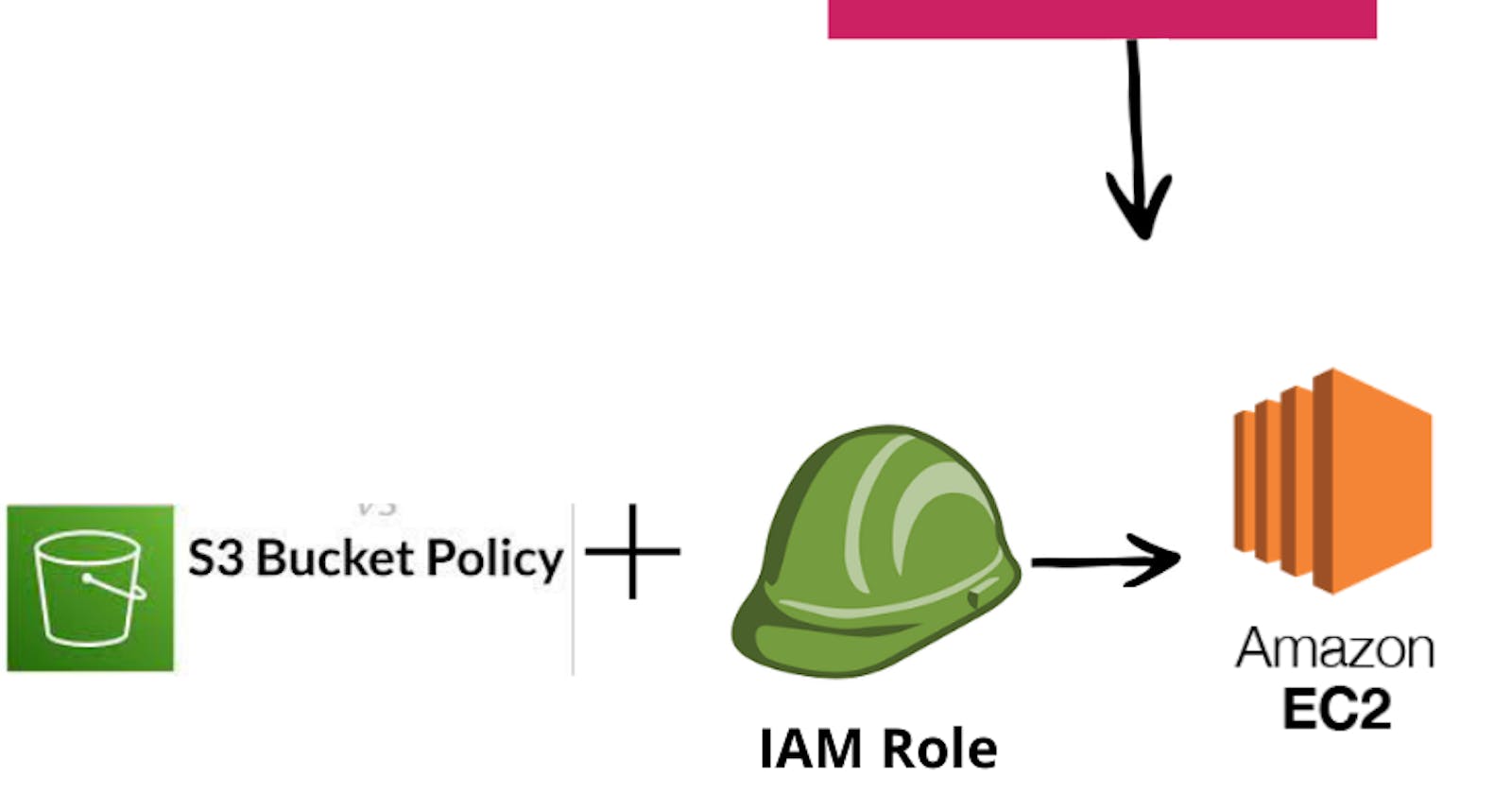
Automating AWS EC2 Instance Deployment with CloudFormation: Attaching IAM Role and Policy for Seamless S3 Bucket Access
Introduction :-
CloudFormation template is a powerful tool for orchestrating infrastructure deployment on #Amazon Web Services (AWS). It enables the creation of an #Amazon Elastic Compute Cloud (EC2) instance and the configuration of an associated #Identity and Access Management (IAM) role, along with permissions for accessing an S3 bucket. This template streamlines the process of setting up AWS resources, ensuring that they are provisioned with consistency and repeatability.
Pre-requestisites :-
- Aws account with proper permissions.
CloudFormation template is used to create an #AWS CloudFormation stack that launches an #EC2 instance and attaches an IAM role to it, as well as an IAM policy for accessing an #S3 bucket. Let me provide an overview of the template’s components:
- Parameters: These are input parameters that can be customized when creating the stack. In this template, there are three parameters:
ImageId: The ID of the Amazon Machine Image (AMI) to use for the EC2 instance. It has a default value set to an AMI in the Ireland (eu-west-1) region.AvailabilityZone: The availability zone into which the instance will be launched, with a default value of 'ap-south-1a'.InstanceType: The instance type for the EC2 instance, with a default value of 't2.micro'.
2. Resources: These are the AWS resources that the CloudFormation stack will create. Here’s what’s defined in this section:
MyKeyPair: An EC2 Key Pair that can be used for SSH access to the EC2 instance.DemoInstance: An EC2 instance that uses the specified AMI, instance type, and availability zone. It also references theDemoInstanceProfilefor the IAM role.DemoInstanceProfile: An IAM instance profile that the EC2 instance will assume. It's associated with theDemoEc2InstanceRole.DemoEc2InstanceRole: An IAM role that specifies permissions and trusts the EC2 service to assume the role.DemoInstanceS3Policy: An IAM policy that allows the EC2 instance to access S3 resources within a specific S3 bucket (demo-s3-bucket). This policy is associated with theDemoEc2InstanceRole.
3. Outputs: The DemoInstanceId output provides the instance ID of the created EC2 instance.
When you create a CloudFormation stack using this template, it will launch an EC2 instance with the specified configuration and attach an IAM role that allows it to access the specified S3 bucket. The EC2 instance will also have an associated EC2 Key Pair for secure access.
Make sure to customize the parameters as needed, such as changing the ImageId, AvailabilityZone, and InstanceType, according to your specific requirements.
Deployment Steps :
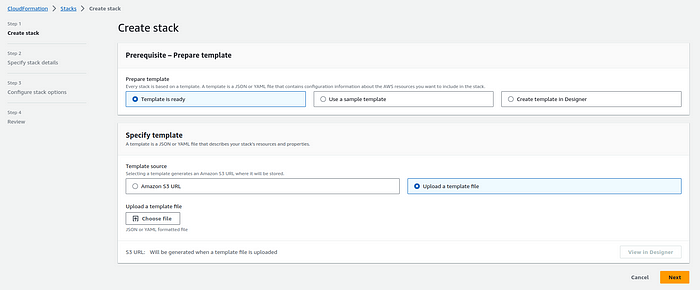
Follow these steps to upload and create the CloudFormation stack using the #AWS Management Console:
- Sign in to the AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the #AWS CloudFormation service from the AWS Management Console.
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
Yaml :
AWSTemplateFormatVersion: '2010-09-09'
Description: Template to attach an IAM role to an EC2 instance
Parameters:
ImageId:
Type: String
Description: 'Linux 2 AMI for Ireland eu-west-1 Region'
Default: 'ami-123456789'
AvailabilityZone:
Type: String
Description: Availability Zone into which instance will launch
Default: ap-south-1a
InstanceType:
Type: String
Description: Choosing t2 micro because it is free
Default: t2.micro
Resources:
MyKeyPair:
Type: 'AWS::EC2::KeyPair'
Properties:
KeyName: MyKeyPairName
DemoInstance:
Type: 'AWS::EC2::Instance'
Properties:
ImageId: !Ref ImageId
InstanceType: !Ref InstanceType
AvailabilityZone: !Ref AvailabilityZone
KeyName: "MyKeyPairName"
IamInstanceProfile: !Ref DemoInstanceProfile
DemoInstanceProfile:
Type: AWS::IAM::InstanceProfile
Properties:
InstanceProfileName: demo-ec2-instance-profile
Path: /
Roles:
- !Ref DemoEc2InstanceRole
DemoEc2InstanceRole:
Type: AWS::IAM::Role
Properties:
RoleName: demo-ec2-instance-role
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
-
Effect: Allow
Principal:
Service:
- ec2.amazonaws.com
Action:
- sts:AssumeRole
Path: /
DemoInstanceS3Policy:
Type: AWS::IAM::Policy
Properties:
PolicyName: DemoS3Policy
PolicyDocument:
Version: 2012-10-17
Statement:
-
Effect: Allow
Action:
- s3:*
Resource:
- arn:aws:s3:::demo-s3-bucket/*
- arn:aws:s3:::demo-s3-bucket
Roles:
-
!Ref DemoEc2InstanceRole
Outputs:
DemoInstanceId:
Description: Instance Id
Value: !Ref DemoInstance
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion :-
CloudFormation template serves as a valuable blueprint for automating the deployment of an #EC2 instance and associated #IAM resources within an #AWS environment. By utilizing the template, users can significantly simplify the management of their infrastructure, enhancing both security and operational efficiency. The structured approach to resource provisioning ensures that configurations are reproducible and consistent, making it a robust solution for anyone looking to establish a foundation for AWS-based applications and services.