Automating CI/CD Pipeline Creation with AWS CloudFormation and AWS CodeBuild
Introduction:
#AWS (Amazon Web Services) offers a wide range of tools and services to streamline the deployment process, and one of the key services for infrastructure as code is AWS CloudFormation. In this document, we will explore an #AWS CloudFormation template designed to create a #CI/CD (Continuous Integration and Continuous Deployment) pipeline using #AWS CodeBuild. This template is an essential building block for automating the deployment of applications and infrastructure in a systematic and efficient manner.
This template is used to define and provision AWS resources for a CI/CD pipeline using AWS CodeBuild to execute a stack.
Here’s a breakdown of the key components in this CloudFormation template:
AWSTemplateFormatVersion: This specifies the version of the CloudFormation template format.
Description: A brief description of the purpose of the CloudFormation template.
Parameters: These are input parameters for the template. Users are prompted to provide values for these parameters when creating a stack.
ApplicationName: A string parameter used for naming the pipeline and build resources.GitHubOAuthTokenSecretName: A string parameter, potentially used for GitHub OAuth token information.GitHubRepositoryOwner: The GitHub username of the repository owner.GitHubRepository: The name of the GitHub repository to be monitored for changes.
4. Resources: These are the AWS resources that the CloudFormation stack will create. Here are some of the key resources:
ArtifactS3Bucket: An AWS S3 bucket used for storing artifacts related to the CodeBuild project.CodeBuildRole: An AWS Identity and Access Management (IAM) role used by AWS CodeBuild.CodeBuildIAMPolicy: An IAM policy attached to the CodeBuild role, defining permissions.CodeBuild: The AWS CodeBuild project definition, specifying build details and environment configurations.
The IAM policy (CodeBuildIAMPolicy) allows the CodeBuild project to perform actions related to logging, S3 access, AWS Secrets Manager, CloudFormation, IAM, KMS, SNS, and other AWS services.
The CodeBuild resource specifies details of the CodeBuild project, including the source location (GitHub repository), build specifications, and environment variables.
Deployment Steps
Follow these steps to upload and create the #CloudFormation stack using the #AWS Management Console:
- Sign in to the AWS Management Console: Log in to your #AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the #AWS CloudFormation service from the AWS Management Console.
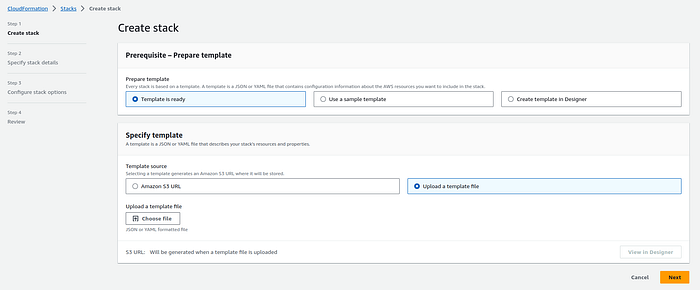
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
Yaml :
AWSTemplateFormatVersion: 2010-09-09
Description: >-
AWS CloudFormation Template for CI/CD pipeline of codebuild project to execute
the stack.
Parameters:
ApplicationName:
Description: This will be used to name the pipeline and build resources
Type: String
AllowedPattern: '[A-Za-z0-9-]+'
GitHubOAuthTokenSecretName:
Type: String
GitHubRepositoryOwner:
Description: Enter GitHub username of the repository owner
Type: String
GitHubRepository:
Description: Enter the repository name that should be monitored for changes
Type: String
Resources:
ArtifactS3Bucket:
Type: 'AWS::S3::Bucket'
Properties:
BucketName: !Join
- '-'
- - codebuild
- !Ref ApplicationName
CodeBuildRole:
Type: 'AWS::IAM::Role'
Properties:
Path: /
RoleName: !Sub '${ApplicationName}-CodeBuild-Pipeline'
AssumeRolePolicyDocument:
Statement:
- Action: 'sts:AssumeRole'
Effect: Allow
Principal:
Service: codebuild.amazonaws.com
CodeBuildIAMPolicy:
Type: 'AWS::IAM::Policy'
Properties:
PolicyName: !Sub '${ApplicationName}-CodeBuildPolicy-Pipeline'
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Resource:
- '*'
Action:
- 'logs:CreateLogGroup'
- 'logs:CreateLogStream'
- 'logs:PutLogEvents'
- Effect: Allow
Resource:
- !Join
- ''
- - 'arn:aws:s3:::'
- !Ref ArtifactS3Bucket
- /*
Action:
- 's3:GetObject'
- 's3:GetObjectVersion'
- 's3:PutObject'
- Effect: Allow
Resource:
- !Sub >-
arn:aws:secretsmanager:${AWS::Region}:${AWS::AccountId}:secret:github-token*
Action:
- 'secretsmanager:GetSecretValue'
- Effect: Allow
Resource:
- '*'
Action:
- 'cloudformation:*'
- Effect: Allow
Resource:
- '*'
Action:
- 'iam:*'
- 'kms:*'
- 'sns:*'
- 's3:*'
- 'codebuild:*'
- 'codepipeline:*'
- 'events:*'
Roles:
- !Ref CodeBuildRole
CodeBuild:
Type: 'AWS::CodeBuild::Project'
Properties:
Name: !Sub '${ApplicationName}'
Description: !Sub 'Build project of ${ApplicationName} '
Source:
BuildSpec: 'build-config/build-spec.yml'
GitCloneDepth: 1
GitSubmodulesConfig:
FetchSubmodules: false
InsecureSsl: false
Location: !Sub https://github.com/${GitHubRepositoryOwner}/${GitHubRepository}
ReportBuildStatus: false
Type: 'GITHUB'
SourceVersion: !Sub refs/heads/master
Artifacts:
Type: 'NO_ARTIFACTS'
Cache:
Type: 'NO_CACHE'
ServiceRole: !Ref CodeBuildRole
Environment:
ComputeType: BUILD_GENERAL1_SMALL
PrivilegedMode: false
Image: 'aws/codebuild/standard:5.0'
Type: LINUX_CONTAINER
EnvironmentVariables:
- Name: STACK
Type: 'PLAINTEXT'
Value: none
- Name: STACKTYPE
Type: 'PLAINTEXT'
Value: pipeline
5. Specify Stack Details:
Enter a Stack name for your #deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the #deployment.
7. Monitor Stack Creation:
The #CloudFormation stack creation process will begin.
Monitor the stack events in the #AWS Management Console.
Conclusion:
#AWS CloudFormation template presented in this document serves as a powerful tool for organizations looking to enhance their #software development and deployment processes. By using this template, teams can establish a robust #CI/CD pipeline that automates the build and deployment of applications with the help of #AWS CodeBuild. This not only accelerates the delivery of software but also ensures consistency and reliability in the deployment process. As technology and business requirements continue to evolve, having the ability to adapt and #automate is essential, and #AWS CloudFormation is a key enabler in achieving these objectives. With this template as a foundation, organizations can take significant strides toward modernizing their software development and deployment practices within the AWS ecosystem.