Automating Serverless Operations: Deploying AWS Resources with CloudFormation for Lambda Functions and CloudWatch Alarms

Introduction :-
#AWS CloudFormation is a powerful #infrastructure-as-code (IaC) service offered by #Amazon Web Services (AWS) that simplifies the provisioning and management of #AWS resources. It enables users to define their infrastructure requirements in a declarative template, #automating the creation, update, and deletion of resources in a predictable and repeatable manner.
This #AWS CloudFormation script is designed to facilitate the #deployment of #AWS resources essential for a serverless #Lambda function. #Serverless computing is a paradigm shift in #cloud computing, allowing developers to focus solely on writing code while #AWS takes care of the underlying infrastructure. Within this script, not only is the #Lambda function provisioned, but it also includes the configuration of associated #CloudWatch Alarms for monitoring and alerting.
AWS CloudFormation Template
#AWSTemplateFormatVersion: Specifies the format version of the #CloudFormation template.
#Transform: Specifies the transformation used. In this case, it’s using the #AWS Serverless Application Model (AWS SAM) with version 2016–10–31.
Description: Provides a description of the #CloudFormation template.
Parameters
This section defines the input parameters for the #CloudFormation template. Input parameters allow customization when creating or updating the #stack.
EnvironmentName: The environment name for the application.
#ApplicationName: The name of the application.
CodeS3Bucket: The name of the #S3 bucket where the #Lambda function’s artifacts are stored.
CodeS3Key: The #S3 key for the Lambda artifact.
#AccountId: The #AWS account from which #SQS messages are to be replicated.
Deployment Steps
Follow these steps to upload and create the #CloudFormation stack using the #AWS Management Console:
- Sign in to the #AWS Management Console: Log in to your #AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the AWS CloudFormation service from the #AWS Management Console.
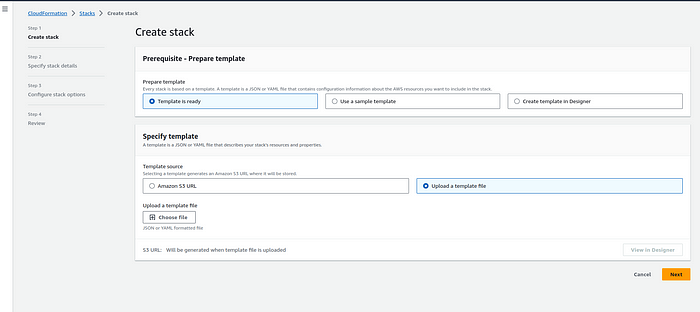
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
lambda.yaml
AWSTemplateFormatVersion: '2010-09-09'
Transform: AWS::Serverless-2016-10-31
Description: Serverless Lambda function
Parameters:
EnvironmentName:
Description: Environment name for the application
Type: String
ApplicationName:
Description: Application Name
Type: String
CodeS3Bucket:
Description: S3 Bucket in which the artifacts are stored
Type: String
MinLength: 3
CodeS3Key:
Description: S3 Key for the lambda artifact
Type: String
MinLength: 3
AccountId:
Description: The AWS account from where the SQS messages are to be replicated
Type: String
MinLength: 1
Mappings: {}
Conditions: {}
Resources:
LambdaFunction:
Type: AWS::Serverless::Function
DependsOn:
- LambdaSecurityGroup
Properties:
CodeUri:
Bucket: !Ref CodeS3Bucket
Key: !Ref CodeS3Key
Handler: index.Hander
MemorySize: 128
Runtime: nodejs14.x
Timeout: 30
Policies:
- AWSLambdaVPCAccessExecutionRole
- Version: '2012-10-17'
Statement:
- Effect: Allow
Action:
- sqs:ChangeMessageVisibility
- sqs:ChangeMessageVisibilityBatch
- sqs:DeleteMessage
- sqs:DeleteMessageBatch
- sqs:PurgeQueue
- sqs:ReceiveMessage
Resource: !Sub arn:aws:sqs:${AWS::Region}:${AccountId}:*
- Effect: Allow
Action:
- sns:Publish
Resource: !Sub arn:aws:sns:${AWS::Region}:${AWS::AccountId}:*
- Effect: Allow
Action:
- secretsmanager:DescribeSecret
- secretsmanager:GetSecretValue
- secretsmanager:ListSecretVersionIds
- secretsmanager:ListSecrets
Resource: !Sub arn:aws:secretsmanager:${AWS::Region}:${AWS::AccountId}:secret:${EnvironmentName}-mahiratech-secrets*
FunctionName: !Sub ${EnvironmentName}-${ApplicationName}
Events:
SQSTaskScheduler:
Type: Schedule
Properties:
Schedule: rate(1 minute)
LambdaAlarm:
Type: AWS::CloudWatch::Alarm
Properties:
AlarmName: !Sub ${EnvironmentName}-SQSLambdaAlarmForError
AlarmDescription: Alarm if lambda errors out too many times
Namespace: AWS/Lambda
MetricName: Errors
Dimensions:
- Name: FunctionName
Value: !Ref LambdaFunction
Statistic: Average
ComparisonOperator: GreaterThanThreshold
Threshold: '10'
EvaluationPeriods: '5'
Period: '60'
DependsOn:
- LambdaFunction
Outputs:
LambdaFunctionConsoleUrl:
Description: Console URL for the Lambda Function.
Value: !Join
- ''
- - https://
- !Ref AWS::Region
- ".console.aws.amazon.com/lambda/home?region="
- !Ref AWS::Region
- "#/functions/"
- !Ref LambdaFunction
5. Specify Stack Details:
Enter a Stack name for your #deployment.
Provide parameter values as needed.
#Review and acknowledge the capabilities (if required).
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the #stack details and #configuration.
Click “Create stack” to initiate the #deployment.
7. Monitor Stack Creation:
The #CloudFormation stack creation process will begin.
#Monitor the stack events in the #AWS Management Console.
Conclusion :-
#AWS CloudFormation plays a pivotal role in modern cloud #infrastructure management by providing a standardized and automated approach to defining and deploying #AWS resources. The #CloudFormation script presented here exemplifies its capabilities in provisioning a serverless Lambda function, an integral component of many #serverless applications.
By using this script, #AWS users can expedite the #deployment process while ensuring consistency and reliability. Moreover, the inclusion of #CloudWatch Alarms in the script demonstrates the importance of #monitoring and alerting in maintaining the health and performance of #AWS resources.
