AWS IAM Permissions Boundaries: Elevate Security and Control in Your Cloud Infrastructure

OverView :-
#AWS Identity and Access Management (IAM) is a powerful service that helps you control access to AWS resources. One advanced feature within IAM is “Permissions Boundaries.” This feature allows you to set the maximum permissions that an #IAM entity (user or role) can have. Let’s dive into what Permissions Boundaries are, why they are important, and how to use them effectively.
What are Permissions Boundaries and why to use permissions Boundaries:-
Allow you to delegate permission to create users and roles while preventing privilege escalation or unnecessarily broad permissions. Permission boundaries control the maximum permissions of a user or role created by a delegated admin.
Granular Control: Permissions Boundaries allow you to delegate permissions management while still maintaining a strict limit on what actions can be taken.
#Security: By limiting excessive permissions, Permissions Boundaries minimize the risk of accidental or intentional misuse of privileges.
Compliance: In #scenarios where separation of duties is required, Permissions Boundaries ensure that certain tasks are restricted, even if policies allow them.
Pre-requestisites:-
- Aws account with required permissions.
Steps to create Permissions Boundaries for an #IAM User :-
Step-1 :- Login to your aws management console and navigate to #Identity and Access Management service, Next click on users and Add users.

Step-2 :- Enter the user details and confirm to next

Step-3 :- Now u need to set the permissions Boundaries for the user. Select the required permissions u want to give for the user and click on create user.

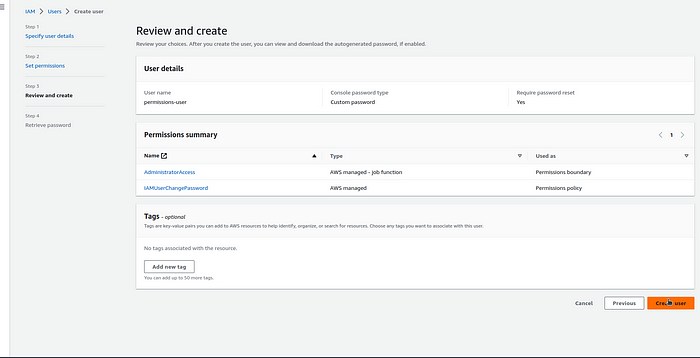
Step-4 :- After the user is being created, check the permission boundaries u have been set for the user as shown like below.

Conclusion :-
#AWSIAM Permissions Boundaries provide an added layer of control and #security in your AWS environment. By defining maximum permissions for #IAM entities, you ensure that even in situations of policy misconfigurations or over-entitlements, the potential impact is limited. Leverage Permissions Boundaries to enforce the least privilege principle and enhance your access management #strategy.
