Demystifying AWS CloudFormation: Crafting Amazon ECS Task Definitions for Optimal AWS Fargate Deployment

Introduction :-
AWS CloudFormation template is designed to facilitate the provisioning of an #Amazon ECS Task Definition suitable for #AWS Fargate. The template includes parameters for customizing the task definition, such as CPU and memory allocation, Docker image, port mappings, and environment variables. It also provides options for securely managing sensitive information using #AWS Secrets Manager and configuring CloudWatch Logs for container logging.
Resources: In this section, you can define AWS resources like I#AM roles and the ECS Task Definition itself. Be sure to customize the permissions and policies for the IAM roles according to your application’s needs.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the #AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to #CloudFormation: Go to the #AWS CloudFormation service from the AWS Management Console.
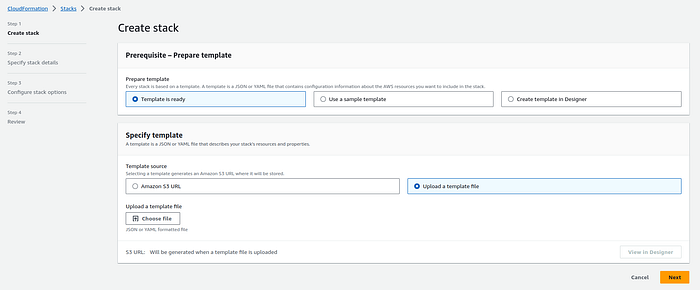
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
AWSTemplateFormatVersion: '2010-09-09'
Description: An AWS CloudFormation template defining an Amazon ECS Task Definition with CloudWatch Logs configuration.
Parameters:
ApplicationName:
Type: String
Description: The name or family of the task definition.
ContainerCpu:
Type: String
Description: The amount of CPU to allocate to the container.
ContainerMemory:
Type: String
Description: The amount of memory to allocate to the container.
ContainerImage:
Type: String
Description: The Docker image to use for the container.
ContainerPort:
Type: String
Description: The port to map from the container to the host.
EnvironmentName:
Type: String
Description: The value for the NODE_ENV environment variable.
AurorMySQLUserArn:
Type: String
Description: The AWS Secrets Manager ARN for the database user.
AurorMySQLPasswordArn:
Type: String
Description: The AWS Secrets Manager ARN for the database password.
CloudwatchLogsGroup:
Type: String
Description: The name of the CloudWatch Logs group for container logs.
Resources:
EcsTaskExecutionRole:
Type: AWS::IAM::Role
Properties:
# Define the permissions and policies for the execution role.
EcsTaskRole:
Type: AWS::IAM::Role
Properties:
# Define the permissions and policies for the task role.
EcsTaskDefinition:
Type: AWS::ECS::TaskDefinition
Properties:
Family: !Ref ApplicationName
Cpu: !Ref ContainerCpu
Memory: !Ref ContainerMemory
NetworkMode: awsvpc
RequiresCompatibilities:
- FARGATE
ExecutionRoleArn: !GetAtt EcsTaskExecutionRole.Arn
TaskRoleArn: !GetAtt EcsTaskRole.Arn
ContainerDefinitions:
- Name: !Ref ApplicationName
Cpu: !Ref ContainerCpu
Memory: !Ref ContainerMemory
Image: !Ref ContainerImage
StopTimeout: 60
PortMappings:
- ContainerPort: !Ref ContainerPort
HostPort: !Ref ContainerPort
Environment:
- Name: NODE_ENV
Value: !Ref EnvironmentName
Secrets:
- Name: PS_USER
ValueFrom: !Ref AurorMySQLUserArn
- Name: PS_PW
ValueFrom: !Ref AurorMySQLPasswordArn
LogConfiguration:
LogDriver: awslogs
Options:
awslogs-group: !Ref CloudwatchLogsGroup
awslogs-region: !Sub "${AWS::Region}"
awslogs-stream-prefix: ecs
Outputs:
TaskDefinitionArn:
Description: The ARN of the created Amazon ECS Task Definition.
Value: !Ref EcsTaskDefinition
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion :-
By using this CloudFormation template, you can streamline the process of setting up and managing ECS task definitions for your containerized applications. The template provides a structured and easily customizable way to specify key parameters and resources, facilitating the deployment of containers on #AWS Fargate with integrated logging and secret management.
