Introduction :-
Enabling Session Manager on an #EC2 instance involves creating an #IAM instance profile with the required #permissions and then associating that profile with the EC2 instance. Follow the steps below to set up Session Manager on your EC2 instance:
Prerequisites:
An AWS account
AWS CLI installed and configured
#Terraform installed on your machine
First we need to Create #IAM instance profile with Session Manager permissions. Follow the below steps to do it.
Step-1:- Go to the #IAM (Identity and Access Management) console: https://console.aws.amazon.com/iam/
Step-2:- Click on “Roles” in the left sidebar and then click on “Create role”.
Step-3:- For “Select type of trusted entity”, choose “AWS service” and then “EC2” as the trusted entity . Click “Next: Permissions”.
Step-4:- In the “Attach permissions policies” search box, type “AmazonSSMManagedInstanceCore” and check the box next to it. This policy provides the necessary permissions for Session Manager.
Step-5:- Alternatively, if you need to grant all Systems Manager permissions, you can attach the “AmazonSSMFullAccess” policy instead.
Step-6:- Click “Next: Tags” to add any relevant tags if needed. Provide a name for the role and optionally add a description.Then Click on “Create role” to create the IAM instance profile.
- Associate the newly created #IAM role with your EC2 instance:
Step-7:- Go to the EC2 Instances page:https://console.aws.amazon.com/ec2/. and Select the EC2 instance you want to enable Session Manager for by checking the checkbox next to it.
Step-8:- Click on “Actions” in the upper menu, then select “Instance Settings”, and finally click on “Modify IAM role”.
Step-9:- In the “IAM role” dropdown, select the #IAM role you created in the previous step.Next Click “Save” to associate the role with the instance.
- Connect to your instance using Session Manager:
Step-10:- In the #EC2 Instances page, select the instance for which you enabled Session Manager. Click on “Connect” at the top of the page.
Step-11:- In the “Connect to instance” section, choose the “Session Manager” tab. Click on the “Connect” button to initiate the Session Manager connection to the instance.
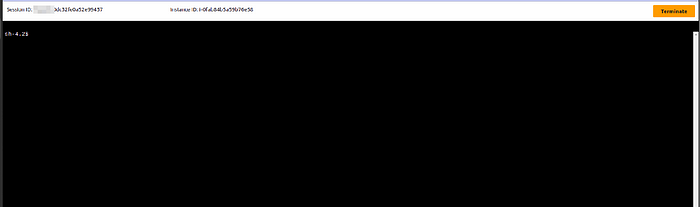
Step-12:- A new browser window will open, showing the command-line interface of your EC2 instance through Session Manager like below.
You can also enable the ssm on ec2 instance using #IAC tool as shown like below.
#Terraform script for Enabling Session Manager on an EC2 instance :-
Step-1 :- Create a directory named session-manager in your home directory and within the session-manager folder create terraform configuration files such as main.tf.
Step-2 :- paste the below code into main.tf and open a terminal window then configure your aws credentials, then deploy your code.
# Create IAM Instance Profile
resource "aws_iam_role" "instance_profile" {
name = "MySSMInstanceProfile"
assume_role_policy = jsonencode({
Version = "2012–10–17"
Statement = [
{
Action = "sts:AssumeRole"
Effect = "Allow"
Principal = {
Service = "ec2.amazonaws.com"
}
}
]
})
}
resource "aws_iam_role_policy_attachment" "instance_profile_attachment" {
policy_arn = "arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore" # Use "AmazonSSMFullAccess" for full Systems Manager permissions
role = aws_iam_role.instance_profile.name
}
# Replace "YOUR_INSTANCE_ID" with your EC2 instance ID
resource "aws_instance" "example" {
ami = "ami-xxxxxxxxx" # Replace with your desired AMI ID
instance_type = "t2.micro" # Replace with your desired instance type
iam_instance_profile = aws_iam_role.instance_profile.name
tags = {
Name = "ExampleInstance"
}
}
Step-3 :- Once the deployment is done, connect to your instance using session manager.
Conclusion:-
That’s it! You have now successfully set up and connected to your #EC2 instance using #AWS Systems Manager Session Manager. This method allows you to access your instances without the need for #SSH/RDP, making it more #secure and manageable.
