How Terraform Can Revolutionize Your AWS SES Domain Identity Configuration

Overview :-
When setting up email services in the cloud using AWS Simple Email Service (SES), one of the first hurdles is configuring your domain identity. Here’s where Terraform, an open-source infrastructure as code software tool, really shines. Terraform can automate the domain verification process and the setup of DKIM (DomainKeys Identified Mail) records for your SES. Imagine replacing the manual, error-prone processes with a few lines of readable, version-controlled code. That’s the power of using Terraform for your AWS SES configuration!
Pre-requisites :-
Before diving into the specifics, let’s ensure you have everything needed to start:
AWS Account: Your gateway to accessing AWS SES.
Terraform installed: Check the latest version is installed on your machine.
Basic understanding of AWS SES: Know its roles in email services.
Familiarity with DNS management: Since you’ll be modifying DNS settings.
Procedure :-
Step 1: Set Up Terraform Provider
Firstly, create a folder with name ses_identity. within the folder create terraform configuration files such as main.tf, variables.tf, provider.tf and define your Terraform provider and authenticate it to use your AWS resources. This involves specifying your access key, secret key, and the region where your SES is hosted.
#provider.tf
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.47.0"
}
}
}
provider "aws" {
region = "us-east-1"
access_key = "your-access-key"
secret_key = "your-secret-key"
}
Step 2: Configure SES Domain Identity and Verify the Domain
Next, copy the below terraform script into the main.tf file to declare your domain identity. This script instructs AWS SES that you own the specified domain.
#main.tf
resource "aws_ses_configuration_set" "ses_config" {
name = "config_ses"
reputation_metrics_enabled = true
}
resource "aws_ses_domain_identity" "domain_identity" {
domain = var.domain_name
}
resource "aws_ses_domain_dkim" "dkim_identity" {
domain = aws_ses_domain_identity.domain_identity.domain
}
resource "aws_route53_record" "amazonses_dkim_record" {
count = 3
zone_id = aws_route53_zone.route_53_zone.zone_id
name = "${aws_ses_domain_dkim.dkim_identity.dkim_tokens[count.index]}._domainkey.${aws_ses_domain_identity.domain_identity.domain}"
type = "CNAME"
ttl = "300"
records = ["${aws_ses_domain_dkim.dkim_identity.dkim_tokens[count.index]}.dkim.amazonses.com"]
}
resource "aws_ses_domain_identity_verification" "domain_identity_verification" {
domain = aws_ses_domain_identity.domain_identity.id
depends_on = [aws_route53_record.amazonses_dkim_record]
}
resource "aws_ses_email_identity" "email_identity" {
email = "contact@mahiratechnology.com"
}
resource "aws_route53_zone" "route_53_zone" {
name = var.domain_name
}
#variables.tf
variable "domain_name" {
type = string
default = "yourdomain.com"
}
Here you’ll replace "yourdomain.com" with your actual domain.
Step 3: Deploy the terraform configuration
- Open a command prompt or terminal window and navigate to your ses_identity folder. Next configure aws credentials and run “terraform init” command to initialize your terraform configuration. Next run “terraform plan” and then “terraform apply” command to deploy your terraform configuration.
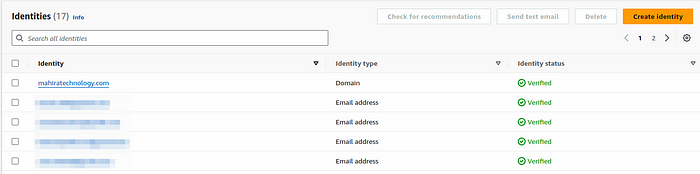
Step 4: Verify the configuration
- Once the deployment is done. Login to your aws account and verify your ses domain configuration.
Conclusion :-
Setting up domain identity for AWS SES using Terraform not only simplifies the entire process but also ensures it’s reproducible and accurate. No more manual record entries or missed updates in DNS. With these steps, your email systems are primed for reliability and high deliverability.
Ready to make the switch, streamline your AWS SES setup, and stay worry-free about email system subtleties? Terraform and its straightforward scripts have got your back!
