Overview
Trivy is an open-source vulnerability scanner for container images. By integrating Trivy into your CI/CD pipeline, you can identify and address security vulnerabilities in your Terraform modules.
In this document, we will walk through the steps to implement Trivy vulnerability scanning on Terraform modules using #CircleCI.
Prerequisites
#CircleCI: Set up a CircleCI account and connect it to your GitHub repository.
Trivy: Install Trivy on your local development machine or set it up as a Docker container in your CI/CD environment.
Step 1: Configure Terraform Modules
Create or navigate to the directory containing your Terraform modules.
Ensure that your Terraform modules are structured properly and contain all the necessary files, such as
.tffiles, variables, and providers.
Step 2: Set up Trivy
Install Trivy on your local development machine or set up a Trivy Docker container in your CI/CD environment. Refer to the Trivy documentation for installation instructions.
Verify that Trivy is working correctly by running a vulnerability scan on a container image or an example Terraform module.
Step 3: Configure CircleCI
In your GitHub repository, create a folder named .#Circleci within that folder #CircleCI a configuration file named config.yml like this
.circleci/config.yml. This file defines the jobs, workflows, and steps for #CircleCI.Define a new job in the configuration file to run the Trivy vulnerability scan on your Terraform modules.
provide the ./path to your terraform modules. As shown in the below job picture.
trivy:
docker:
- image: aquasec/trivy:latest
working_directory: /tmp/workspace
environment:
ENV_FILE: /tmp/workspace/
DOCKER_BUILDKIT: "1"
BUILDKIT_PROGRESS: plain
steps:
- checkout
- attach_workspace:
at: /tmp/workspace
- setup_remote_docker:
version: 20.10.7
docker_layer_caching: true
- run:
name: Install trivy
command: |
apk add --update-cache --upgrade --update curl
curl -sfL https://raw.githubusercontent.com/aquasecurity/trivy/main/contrib/install.sh | sh -s -- -b /usr/local/bin
- run:
name: Run Trivy Scan
command: |
trivy fs --scanners vuln,secret,config --severity HIGH,CRITICAL,LOW ./path to your terraform modules/ > trivy_output.txt
# Upload the output file to CircleCI artifacts
- store_artifacts:
path: trivy_output.txt
destination: trivy_output
The above example assumes you are running trivy vulnerability scan on your Terraform modules and publishes the scan output as artifact.
Add any additional steps or configurations as required for your CI/CD workflow, such as running Terraform commands, or publishing artifacts.
Step 4: Triggering the Trivy Scan
Commit and push your changes to the GitHub repository.
#CircleCI will automatically detect the changes and trigger a build based on the configuration defined in
.circleci/config.yml.#CircleCI will execute the Trivy vulnerability scan job defined in the configuration file.
Trivy will scan the specified Terraform module for vulnerabilities and generate a report.
you can see the trivy job running in the below figure.
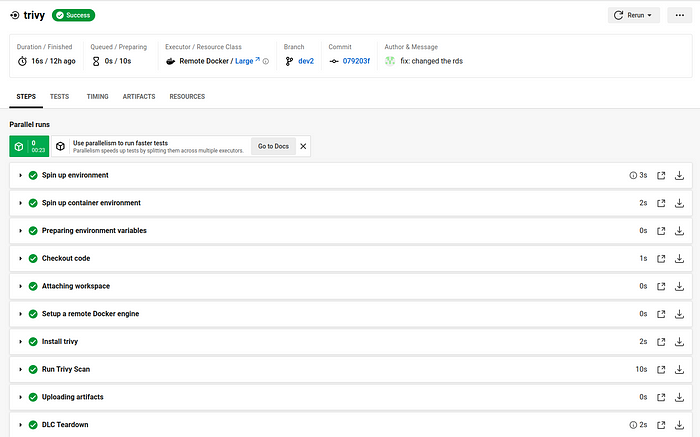
Step 5: Review the Trivy Scan Results
Once the #CircleCI job is complete, navigate to the #CircleCI dashboard or the specific build/job in your browser.
Locate the Trivy scan step within the build logs or artifacts.
you can find the trivy scan result file in the #Circleci artifacts as shown in the below picture.
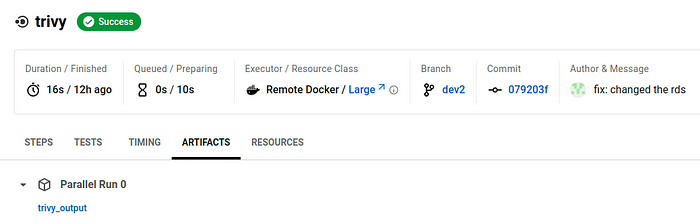
Click on the trivy_output view the results.
Review the Trivy scan results to identify any security vulnerabilities or issues reported for your Terraform modules.
Address the identified vulnerabilities by following best practices for security patching, updating dependencies, or applying mitigations as necessary.
Conclusion
By implementing Trivy vulnerability scanning on your Terraform modules using #CircleCI, you can proactively identify and address security vulnerabilities, ensuring the integrity and security of your infrastructure deployment.
Remember to regularly update Trivy and your vulnerability databases to stay current with the latest security information.
Note: This document provides a general overview and steps for integrating Trivy with Terraform modules using #CircleCI. It’s recommended to refer to the official documentation of each tool (Trivy, Terraform, #CircleCI) for detailed instructions and advanced configuration options.
