Mastering AWS CloudFormation: A Comprehensive Guide to Managing AWS Key Management Service (KMS) Keys

Introduction :-
AWS CloudFormation is a powerful service that allows users to define and provision their infrastructure and resources in a structured and automated way. Templates like the one presented here offer a means to create, manage, and organize AWS resources with code, enabling reproducibility, scalability, and #infrastructure as code (IaC) best practices. In this particular CloudFormation template, the focus is on #AWS Key Management Service (KMS) key management. KMS keys are crucial for securing sensitive data and controlling access to it within various AWS services. This template exemplifies how to create KMS keys and their associated aliases to provide a solid foundation for encryption and security in an AWS environment.
The template you’ve provided creates AWS Key Management Service (KMS) keys and associated aliases for different use cases within an environment. Let’s break down the key components of this template:
AWSTemplateFormatVersion: This specifies the version of the CloudFormation template format that is being used.Description: A description of the template, which states that it's for KMS key management.Parameters: This section defines input parameters that can be customized when creating a stack based on this template. In this case, there is a single parameter namedEnvironmentNamethat represents the environment name for the application. This parameter is of typeString.Resources: This section defines the AWS resources that the template will create. It includes the following resources:
CareChartKmsKey: An AWS KMS key used for CareChart encryption. It has a Key Policy that allows AWS account root user (arn:aws:iam::${AWS::AccountId}:root) full access (kms:*) to the key.CareChartKmsKeyAlias: An alias for theCareChartKmsKey, which has a name derived from theEnvironmentName.CarePathKmsKey: Another KMS key used for CarePath encryption.CarePathKmsKeyAlias: An alias for theCarePathKmsKey, similar toCareChartKmsKeyAlias.FamilyPortalKmsKey: Yet another KMS key, this one used for family portal encryption.FamilyPortalKmsKeyAlias: An alias for theFamilyPortalKmsKey, which also has a name derived from theEnvironmentName.
5. Outputs: This section defines the stack outputs. It exports the ARN of the KMS keys and aliases created in this template for later use in other stacks or resources.
The template creates three KMS keys and their corresponding aliases, making it possible to encrypt data in different contexts within the specified environment. The EnvironmentName parameter is used to customize the alias names and allows for the reuse of the keys and aliases across different environments by changing the parameter value when creating a stack.
Deployment Steps --
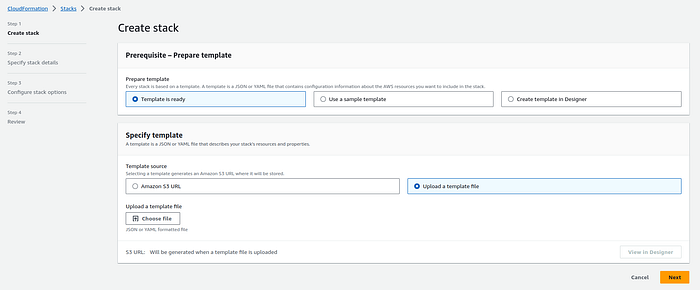
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the AWS CloudFormation service from the AWS Management Console.
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
Yaml:
AWSTemplateFormatVersion: '2010-09-09'
Description: 'KMS key'
Parameters:
EnvironmentName:
Description: Environment name for the application
Type: String
Resources:
CareChartKmsKey:
Type: AWS::KMS::Key
Properties:
Description: "Key used for CareChart encryption"
Enabled: true
KeyPolicy:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
AWS:
Fn::Sub: arn:aws:iam::${AWS::AccountId}:root
Action: kms:*
Resource: "*"
CareChartKmsKeyAlias:
Type: AWS::KMS::Alias
Properties:
AliasName: !Sub 'alias/${EnvironmentName}-KmsKey'
TargetKeyId: !Ref CareChartKmsKey
CarePathKmsKey:
Type: AWS::KMS::Key
Properties:
Description: "Key used for CarePath encryption"
Enabled: true
KeyPolicy:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
AWS:
Fn::Sub: arn:aws:iam::${AWS::AccountId}:root
Action: kms:*
Resource: "*"
CarePathKmsKeyAlias:
Type: AWS::KMS::Alias
Properties:
AliasName: !Sub 'alias/${EnvironmentName}-KmsKey'
TargetKeyId: !Ref CarePathKmsKey
FamilyPortalKmsKey:
Type: AWS::KMS::Key
Properties:
Description: "Key used for family portal encryption"
Enabled: true
KeyPolicy:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
AWS:
Fn::Sub: arn:aws:iam::${AWS::AccountId}:root
Action: kms:*
Resource: "*"
FamilyPortalKmsKeyAlias:
Type: AWS::KMS::Alias
Properties:
AliasName: !Sub 'alias/${EnvironmentName}'
TargetKeyId: !Ref FamilyPortalKmsKey
Outputs:
CarePathKmsKey:
Value:
Fn::GetAtt:
- CarePathKmsKey
- Arn
Export:
Name: !Sub '${EnvironmentName}-KmsKey'
FamilyPortalKmsKey:
Value:
Fn::GetAtt:
- FamilyPortalKmsKey
- Arn
Export:
Name: !Sub '${EnvironmentName}'
CareChartKmsKey:
Value:
Fn::GetAtt:
- CareChartKmsKey
- Arn
Export:
Name: !Sub '${EnvironmentName}'
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion :-
AWS CloudFormation template serves as a valuable blueprint for implementing key management and encryption strategies within AWS. By leveraging KMS keys and aliases, AWS users can ensure that their data remains secure and inaccessible to unauthorized users. The template is designed to be flexible, allowing users to customize it by specifying an environment name, enabling them to deploy the same infrastructure across different environments. In essence, this template demonstrates the power of infrastructure as code, enabling the creation of a secure and standardized environment for your AWS resources, laying the foundation for robust security practices.