Navigating the Complexities of AWS CloudFormation for WAF WebACL: A Beginner’s Blueprint

Introduction :-
AWS CloudFormation is a powerful tool for managing and deploying AWS infrastructure as code. In this #CloudFormation template, we’ve focused on creating a #Web Application Firewall (WAF) WebACL for the Wave App. A WebACL is essential for enhancing the security of your application by defining rules and actions to control and filter incoming web traffic.
This template serves as a foundation for securing your Wave App, but it’s important to note that the provided configuration is just a starting point. You can extend and customize it according to your specific security needs. The template includes basic rules to get you started, such as rate limiting and blocking traffic from certain regions.
In this updated template:
We’ve added two rule definitions:
RateLimitRuleandBlockBadIPsRule.RateLimitRulespecifies a rate-based rule that limits requests to 1000 requests per 5 minutes per IP address.BlockBadIPsRulespecifies a rule that blocks requests from IP addresses that are not in the specified IP set and are not from the United States (US) or Canada (CA).The
GeoMatchStatementis used to match traffic based on the country of origin.
Please note that you’ll need to provide the ARN of the IP set you want to reference in the IPSetReferenceStatement. Additionally, you can customize the rule conditions and actions to meet the specific security requirements of your App.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the AWS CloudFormation service from the AWS Management Console.
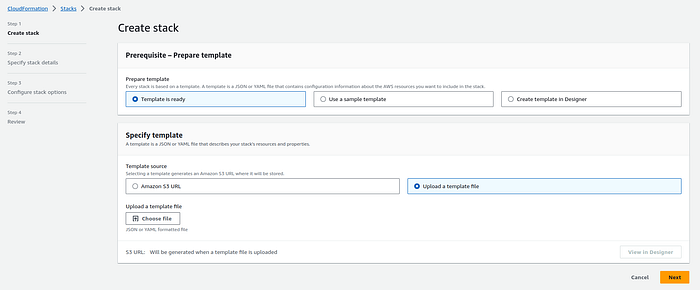
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
AWSTemplateFormatVersion: '2010-09-09'
Resources:
WaveAppWebACL:
Type: "AWS::WAFv2::WebACL"
Properties:
Name: WaveAppWebACL
Scope: CLOUDFRONT
DefaultAction:
Allow: {}
Rules:
- Name: RateLimitRule
Action:
Block: {}
Priority: 1
Statement:
RateBasedStatement:
Limit: 1000
AggregateKeyType: IP
- Name: BlockBadIPsRule
Action:
Block: {}
Priority: 2
Statement:
AndStatement:
Statements:
- IPSetReferenceStatement:
Arn: <your_IPSet_ARN_here>
- NotStatement:
Statement:
GeoMatchStatement:
CountryCodes:
- US
- CA
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion :-
In conclusion, this #CloudFormation template provides a structured and repeatable way to deploy a WebACL for your Wave App. It’s a vital component in securing your web applications from malicious traffic and ensuring that only legitimate requests are allowed through.
To fully secure your application, you may need to add more rules, conditions, and action statements tailored to your unique security requirements. Remember to provide the necessary resources and configuration, such as the ARN of the IP set, and test the WebACL thoroughly to ensure it effectively safeguards your Wave App. AWS CloudFormation simplifies the process of infrastructure deployment and management, allowing you to maintain your security posture as code and keep your Wave App protected.
