Orchestrating the Cloud: A Comprehensive Guide to Creating an AWS EKS Cluster with Terraform

Introduction :-
Embark on a transformative journey into the world of AWS EKS with our comprehensive guide. Discover how to leverage Terraform to effortlessly design and deploy EKS clusters. In this in-depth exploration, we demystify the intricacies of AWS, empowering you to efficiently orchestrate your containerized applications.
Prerequisites :-
- Ensure a smooth start by having Terraform installed on your system. Additionally, configure your AWS account and credentials for seamless integration.
Steps for creating a cluster using terraform :-
Create a folder with name eks_cluster on your Desktop directory. within the eks_cluster folder create terraform configuration files such as main.tf, variable.tf & provider.tf .
Copy and paste the below code into main.tf file.
#main.tf
resource "aws_vpc" "default" {
cidr_block = var.vpc_cidr_block
tags = {
Name = "Mahira-Vpc"
}
}
resource "aws_subnet" "private_subnet" {
count = var.subnet_count
vpc_id = aws_vpc.default.id
cidr_block = var.private_subnets_cidr_blocks[count.index]
availability_zone = var.azs[count.index] # Replace with your desired availability zone
tags = {
Name = "Private Subnet"
}
}
# Create Internet Gateway
resource "aws_internet_gateway" "igw" {
vpc_id = aws_vpc.default.id
tags = {
Name = "Demo IGW"
}
}
# Create Web layber route table
resource "aws_route_table" "web-rt" {
vpc_id = aws_vpc.default.id
route {
cidr_block = "0.0.0.0/0"
gateway_id = aws_internet_gateway.igw.id
}
tags = {
Name = "WebRT"
}
}
resource "aws_security_group" "private_sg" {
vpc_id = aws_vpc.default.id
name = "private_sg"
description = "Allow SSH and http and https"
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "private Security Group"
}
}
resource "aws_iam_role" "eks-cluster-role" {
name = "eks-cluster-role"
assume_role_policy = <<POLICY
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "eks.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
POLICY
}
resource "aws_iam_role_policy_attachment" "AmazonEKSClusterPolicy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKSClusterPolicy"
role = aws_iam_role.eks-cluster-role.name
}
resource "aws_iam_role_policy_attachment" "AmazonEKSServicePolicy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonEKSServicePolicy"
role = aws_iam_role.eks-cluster-role.name
}
resource "aws_security_group" "cluster_sg" {
name = "EKSCluster_SG"
description = "Eks cluster security group"
vpc_id = aws_vpc.default.id
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
tags = {
Name = "sg_for_EKSCluster"
}
}
resource "aws_eks_cluster" "eks_cluster" {
name = "${var.eks_cluster_name}"
role_arn = aws_iam_role.iam-role-eks-cluster.arn
version = var.eks_version
vpc_config { # Configure EKS with vpc and network settings
security_group_ids = [aws_security_group.eks_cluster_sg.id]
subnet_ids = [
aws_subnet.private_subnet[0].id,
aws_subnet.private_subnet[1].id,
aws_subnet.private_subnet[2].id
]
}
depends_on = [
aws_iam_role_policy_attachment.eks-cluster-AmazonEKSClusterPolicy,
aws_iam_role_policy_attachment.eks-cluster-AmazonEKSServicePolicy,
]
tags = {
Name = "${var.eks_cluster_name}"
}
}
#provider.tf
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "5.0.1"
}
kubernetes = {
source = "hashicorp/kubernetes"
version = "2.14.0"
}
}
backend "s3" {
bucket = "Your S3 Bucket Name"
encrypt = true
key = "eks_cluster/terraform.tfstate"
region = "us-east-1"
# Replace this with your DynamoDB table name!
dynamodb_table = "Your DYNAMO-DB Table Name"
}
}
3. create a file with name variable.tf and paste the below code in variable.tf
#variable.tf
variable "subnet_count" {
description = "default count used to set AZs and instances"
type = number
default = 3
}
variable "vpc_cidr_block" {
description = "CIDR block for VPC"
default = "10.0.0.0/16"
}
variable "azs" {
type = list(string)
default = ["us-east-1a", "us-east-1b", "us-east-1c"]
}
variable "private_subnets_cidr_blocks" {
type = list(string)
default = ["10.0.11.0/24", "10.0.12.0/24", "10.0.13.0/24"]
}
variable "eks_cluster_name" {
type = string
description = "eks cluster name"
default = "Mahira-eks-cluster"
}
variable "eks_version" {
type = string
description = "eks version"
default = "1.27"
}
4. Obtain the Output values for the above created resources by creating an outputs.tf file if required.
#outputs.tf
output "cluster_endpoint" {
description = "Endpoint for EKS control plane."
value = aws_eks_cluster.eks_cluster.endpoint
}
output "certificate_authority" {
description = "kubectl config as generated by the module."
value = aws_eks_cluster.eks_cluster.certificate_authority
}
output "cluster_id" {
description = "Cluster id."
value = aws_eks_cluster.eks_cluster.id
}
output "cluster_arn" {
description = "Eks-cluster-arn"
value = aws_eks_cluster.eks_cluster.arn
}
Run Terraform Commands:
Open a terminal, navigate to the ‘eks_cluster’ folder, and configure your AWS credentials.
Execute
terraform initto download necessary packages.Run
terraform planfor a detailed overview of the resources to be created.Execute
terraform applyto create the EKS cluster.
Verify Cluster Creation:
- Login to your AWS account and confirm the successful creation of the EKS cluster using the provided code.
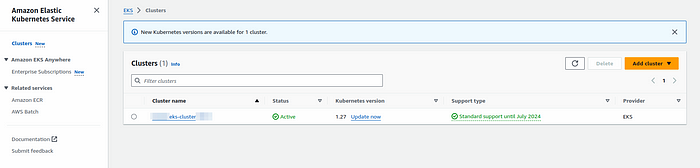
Conclusion :-
Congratulations, you’ve now mastered the art of creating an AWS EKS cluster using Terraform! This journey has equipped you with the skills to not only deploy but also optimize, manage, and troubleshoot your EKS environment effectively. As you embark on your cloud-native adventures, may your EKS clusters thrive, and your applications soar to new heights.
#AWSEKS #Terraform #CloudNative #AWSDeployment #Containerization #InfrastructureAsCode #DevOps #CloudComputing #AWSManagement #KubernetesIntegration #EKSConfiguration #AWSOptimization
