Seamless AWS CloudWatch Alarm Notifications in Microsoft Teams: A Terraform-Driven Integration

Introduction :-
AWS Chatbot is a service provided by #AmazonWebServices (AWS) that enables real-time notifications and interactions with AWS resources through popular chat and collaboration tools. One such integration is with #Microsoft Teams, a widely used team collaboration platform. By setting up #AWS Chatbot with #Microsoft Teams, users can receive #CloudWatch Alarm status notifications directly in their Teams channels, allowing for seamless #monitoring and incident response.
Prerequisites:
An AWS account with required permissions.
#AWS CLI installed and configured
#Terraform installed on your machine
#Microsoft Teams Access
Step-1 :- First,Open your Microsoft Teams and Create a Channel in your micro-soft teams.
Step-2:- Get the channel link from the teams as shown like below

Copy the link, the link will looks like below.
https://teams.microsoft.com/l/channel/19%5e45dew54e6f6ew5f4ewfee6f4f4w%40thread.tacv2/circleci-update?groupId=155e5f151–4f7b-4f8c-5e5f–5e4d56e465f&tenantId=sfd65465-fds07–4937-a846–646465456465
Step-3 :- To create a aws chat-bot using terraform break the channel link into 3 parts (teams_id, teams_channel_id and teams_tenant_id) as shown like below.
From the above link: team_id = 155e5f151–4f7b-4f8c-5e5f–5e4d56e465f
teams_channel_id=19%5e45dew54e6f6ew5f4ewfee6f4f4w%40thread.tacv2
teams_tenant_id = sfd65465-fds07–4937-a846–646465456465
Step-4 :- Create a folder named chat-bot in your home directory and with-in the chat-bot folder create terraform configuration files such as main.tf, variable.tf and outputs.tf. Open the main.tf file using a visual editor and paste the below code into main.tf.
#main.tf
resource "aws_sns_topic" "alarm_notification_teams" {
name = cloudwatch-alarms-notification-teams
}
resource "aws_sns_topic_subscription" "updates_sqs_target" {
topic_arn = aws_sns_topic.alarm_notification_teams.arn
protocol = "https"
endpoint = "https://global.sns-api.chatbot.amazonaws.com"
depends_on = [
aws_sns_topic.alarm_notification_teams
]
}
resource "aws_sns_topic_policy" "notification_teams_policy" {
arn = aws_sns_topic.alarm_notification_teams.arn
policy = data.aws_iam_policy_document.sns_topic_policy.json
}
data "aws_iam_policy_document" "sns_topic_policy" {
policy_id = "alarm-chatbot-sns-policy"
statement {
actions = [
"sns:Publish"
]
effect = "Allow"
principals {
type = "Service"
identifiers = ["cloudwatch.amazonaws.com"]
}
resources = [
aws_sns_topic.alarm_notification_teams.arn,
]
sid = "chatbot-sns-policy"
}
}
resource "aws_iam_role" "chatbot_role" {
name = "alarm-chatbot-role"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "sts:AssumeRole",
"Principal": {
"Service": "chatbot.amazonaws.com"
},
"Effect": "Allow",
"Sid": ""
}
]
}
EOF
}
resource "aws_iam_policy" "chatbot_policy" {
name = "alarm-chatbot-policy"
policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"events:ListRules",
"events:ListTargetsByRule",
"events:DescribeRule"
],
"Effect": "Allow",
"Resource": "*"
}
]
}
EOF
}
resource "aws_iam_role_policy_attachment" "chatbot_attach" {
role = aws_iam_role.chatbot_role.name
policy_arn = aws_iam_policy.chatbot_policy.arn
}
# Copy the above splitted values into the below resource.
resource "awscc_chatbot_microsoft_teams_channel_configuration" "alarm_status" {
configuration_name = "cloudwatch-alarm-notifications-${var.env_name}"
iam_role_arn = aws_iam_role.chatbot_role.arn
team_id = "155e5f151–4f7b-4f8c-5e5f–5e4d56e465f"
teams_channel_id = "19%5e45dew54e6f6ew5f4ewfee6f4f4w%40thread.tacv2"
teams_tenant_id = "sfd65465-fds07–4937-a846–646465456465"
sns_topic_arns = [aws_sns_topic.alarm_notification_teams.arn]
}
resource "aws_cloudwatch_metric_alarm" "ec2-alarm" {
alarm_name = "instance-monitor"
alarm_description = "This alarm will trigger when CPU utilization is Greater Than 80%"
comparison_operator = "GreaterThanOrEqualToThreshold"
evaluation_periods = 1
metric_name = "CPUUtilization"
datapoints_to_alarm = 1
namespace = "AWS/EC2"
period = 60
statistic = "Average"
threshold = 30
alarm_actions = [aws_sns_topic.alarm_notification_teams.arn]
actions_enabled = true
ok_actions = [aws_sns_topic.alarm_notification_teams.arn]
dimensions = {
Instance_id = aws_instance.ec2_instance.id
}
}
resource "aws_instance" "ec2_instance" {
ami = var.ami_id # Replace with your desired AMI ID
instance_type = var.instance_type
key_name = "YOUR-KEYPAIR-NAME"
tags = {
Name = "Alarm-instance"
}
}
# variable.tf
variable "ami_id" {
type = string
default = "ami-xxxxxxxxxxxxxxxxxx"
}
variable "instance_type" {
type = string
default = "t2.micro"
}
Step-5 :- Define the outputs in the output.tf for sns topic and alarms.
#outputs.tf
output "sns_topic_arn" {
description = "sns topic arn"
value = aws_sns_topic.alarm_notification_teams.arn
}
output "arn_prefix" {
description = "sns topic arn prefix"
value = aws_sns_topic.alarm_notification_teams.name_prefix
}
output "chatbot_id" {
description = "chatbot id"
value = awscc_chatbot_microsoft_teams_channel_configuration.alarm_status.id
}
output "alarm_arn" {
description = "this alarm is for ec2 instance"
value = aws_cloudwatch_metric_alarm.ec2-alarm.arn
}
Step-6 :- Before #Deploy the above code, Login to #Aws Management Console and navigate to Aws Chat-bot and configure your MS-Teams in Aws if not configured.
- If Not Configured :- Login to the AWS console and search for Aws ChatBot in search bar. After opening the Aws Chatbot dashboard , click on configure new client. Then select client type as #Microsoft Teams and click on configure.

Once u click on configure it will ask for channel url. Go to the teams and copy the channel url as shown in step-3.
Paste the copied url in the box and once again click on configure.
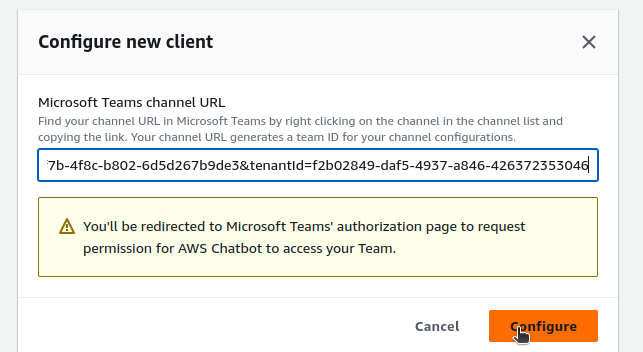
- It will ask for permissions in your micro-soft teams, give the required permissons.
Step-7 :- As u can see that the teams has been configured on aws chat bot.

Step-8 :- After completing the setup of the chatbot client, Open a terminal or command prompt and configue your aws crdentials, then locate to the chat-bot folder and deploy your code using below terraform commands.
terraform init
terraform plan
terraform apply
- After the code is being deployed, open your aws management console and check whether the resources are being created or not.
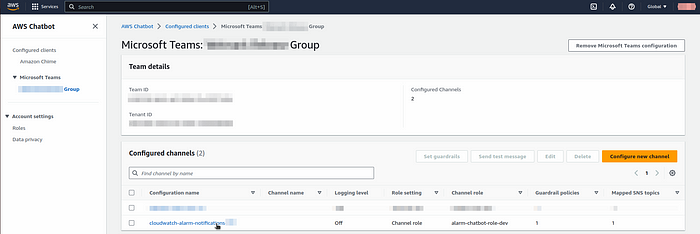
Sep-9:- u can able to see that the alerts channel has been created on chat bot.
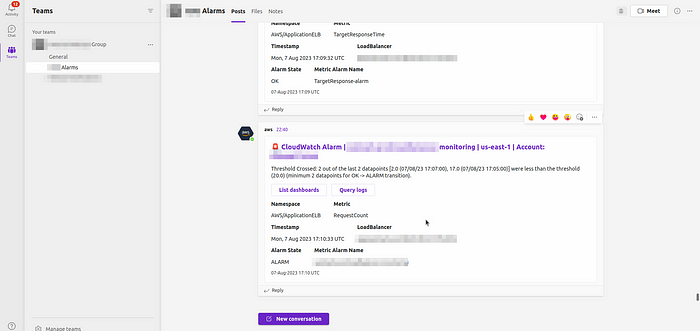
Step-10 :- Once the alarm gets triggered, u can able to get the alerts in teams channel as shown like below.
Conclusion :-
This document outlines the process of #integrating #Microsoft Teams with AWS Chatbot and configuring #Terraform to enable notifications of #CloudWatch alarm statuses in Teams. The integration allows for seamless communication between #AWS Services and Teams, enhancing #monitoring and incident management capabilities. By following the provided steps, users can set up a robust alerting mechanism that ensures timely notifications of #CloudWatch alarms directly in Teams channels.
