Securing AWS Resources: A Guide to IAM User Creation, Access Key Management, and Export with CloudFormation

Introduction :-
AWS CloudFormation template is a fundamental component of AWS infrastructure as code. It outlines the creation of an #AWS Identity and Access Management (IAM) user and its associated access key. This #IAM user, named ‘mahira-User,’ is pivotal for managing access to #AWS resources #securely. #Access keys are often used for programmatic access to #AWS services, making them valuable for automation and integration purposes. In addition, this template defines outputs that are exported for use in other parts of your infrastructure, facilitating seamless access to the created resources.
Here’s a breakdown of the key elements in this #CloudFormation template:
#AWSTemplateFormatVersion: This specifies the version of the AWS #CloudFormation template format being used. In this case, it’s set to ‘2010–09–09’, which is a common choice for CloudFormation templates
#Resources: This section defines the AWS resources that will be created when the #CloudFormation stack is deployed.
IAMUser: This resource defines an IAM user named ‘mahira-User’. #IAM users are used to control access to AWS services and resources. The user is created using the ‘AWS::IAM::User’ resource type.
IAMAccessKey: This #resource creates an access key for the #IAM user defined above. #Access keys are used for programmatic access to #AWS services. The ‘UserName’ property is set to the #IAM user created earlier using the
!Reffunction.
3. Outputs: This section defines what information should be made available as outputs from the #CloudFormation stack.
AccessKeyId: This output is a reference to the ‘IAMAccessKey’ created earlier, and it’s being exported with an export name that’s dynamically generated based on the stack name.
#SecretAccessKey: This output references the ‘IAMAccessKey’ resource and specifically retrieves its ‘#SecretAccessKey’ attribute. It’s also being exported with a dynamically generated export name based on the stack name.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the #AWS Management Console:
- Sign in to the #AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to #CloudFormation: Go to the #AWS CloudFormation service from the #AWS Management Console.
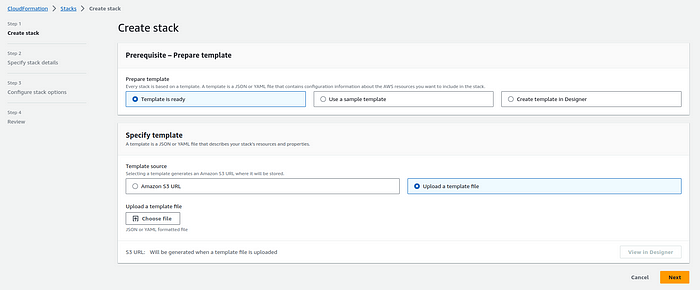
3. Click the “Create stack” button.
4. Upload the #CloudFormation template file (YAML).
Yaml :
AWSTemplateFormatVersion: '2010-09-09'
Resources:
IAMUser:
Type: 'AWS::IAM::User'
Properties:
UserName: 'mahira-User'
IAMAccessKey:
Type: 'AWS::IAM::AccessKey'
Properties:
UserName: !Ref IAMUser
Serial: 1
Outputs:
AccessKeyId:
Value: !Ref IAMAccessKey
Export:
Name: !Sub '${AWS::StackName}-AccessKeyId'
SecretAccessKey:
Value: !GetAtt [IAMAccessKey, SecretAccessKey]
Export:
Name: !Sub '${AWS::StackName}-SecretAccessKey'
5. Specify Stack Details:
Enter a #Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional #stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “#Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The #CloudFormation stack creation process will begin.
Monitor the stack events in the #AWS Management Console.
Conclusion :-
#AWS CloudFormation template serves as a blueprint for provisioning #AWS IAM resources with ease and consistency. By encapsulating the creation of an #IAM user and its access key, it simplifies the process of configuring #user access within your #AWS environment. Furthermore, the template’s export functionality enables the secure dissemination of access key information to other components of your infrastructure. With #CloudFormation, you can efficiently manage your #AWS resources, adhere to #security best practices, and establish a #robust foundation for your cloud-based applications and services.
