Terraform code to create branch protection settings in github

Introduction :-
Using #Terraform to Create Branch Protection Settings in #GitHub are crucial for enforcing certain rules and restrictions on specific branches, ensuring #codequality and preventing unauthorized changes. Terraform provides a powerful toolset for #automating the configuration of branch protection settings in #GitHub, allowing for consistent and efficient management of branch policies across #repositories.
In this guide, we will explore how to utilize Terraform to create branch protection settings in #GitHub. By leveraging Terraform’s #infrastructure-as-code approach, you can define and manage branch protection rules programmatically, enabling easy replication, #version control, and collaboration within your infrastructure workflow.
Pre-Requestsites:-
#Terraform should be installed on your system.
#Github user details should be configured on your machine.
step 1: Open an editor like visualstudio code.
step 2: Create a folder and name it as github-terraform using the same folder create two files named main.tf and variable.tf, provider.tf
step 3: In that main.tf enter the following code:
resource "github_branch_protection" "github_branch_protection" {
repository_id = github_repository.mahira_github.node_id
pattern = "main"
enforce_admins = true
allows_deletions = true
required_status_checks {
strict = false
contexts = ["ci/travis"]
}
required_pull_request_reviews {
dismiss_stale_reviews = true
restrict_dismissals = true
dismissal_restrictions = [
data.github_user.mahira_user.node_id,
github_team.github_team.node_id,
"/MahiraTechnology",
"MahiraTechnology/Mahira team",
]
}
push_restrictions = [
data.github_user.mahira_user.node_id,
"/MahiraTechnology",
"MahiraTechnology/Mahira team",
# limited to a list of one type of restriction (user, team, app)
# github_team.example.node_id
]
force_push_bypassers = [
data.github_user.mahira_user.node_id,
"/MahiraTechnology",
"MahiraTechnology/Mahira team",
# limited to a list of one type of restriction (user, team, app)
# github_team.example.node_id
]
}
resource "github_repository" "mahira_github" {
name = var.repo_name
}
data "github_user" "mahira_user" {
username = var.github_user
}
resource "github_team" "github_team" {
name = var.github_team
}
resource "github_team_repository" "team_repository" {
team_id = github_team.github_team.id
repository = github_repository.mahira_github.name
permission = "pull"
}
- Paste the below code in provider.tf
terraform {
required_providers {
github = {
source = "integrations/github"
version = "5.34.0"
}
}
}
provider "github" {
token = "YOUR GITHUB TOKEN"
}
step 4: In that variable.tf enter the following code:
variable "branch_name" {
description = "Github branch name"
type = string
default = "Development"
}
variable "repo_name" {
type = string
default = "branch-protection"
}
variable "github_user" {
type = string
default = "MahiraTechnology"
}
variable "github_team" {
type = string
default = "Mahira team"
description = "github team"
}
step 5: After successfully code creation .we need the run the code.For that open terminal run first command terraform init.
step 6: After Initialization run second command terraform plan.
step 7: If the plan runs Successfully. Run terraform apply.
step 8: After execution of all those command.login to the github there you can able to see the repository and branches were created.
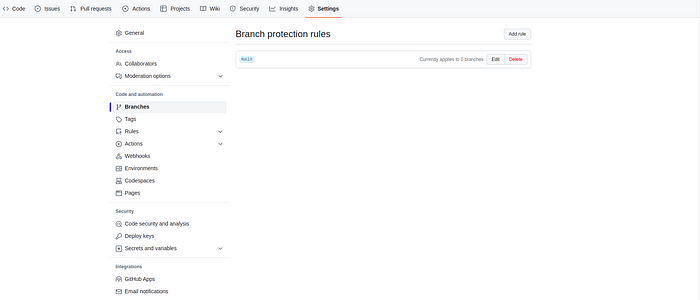
step 9: view the settings in the same repository. you can able to see some of the branch protection were created .
step 10: If no use for repository using terraform destroy you can delete the repository.
Conclusion:-
Terraform’s declarative syntax enables you to define branch protection configurations as code, facilitating version control, repeatability, and easy collaboration. With Terraform, you can efficiently replicate and enforce policies across multiple repositories and environments, ensuring #code quality and reducing the risk of unauthorized or accidental changes.
By automating branch #protection settings using Terraform, you can easily enforce requirements such as required status checks, branch restrictions, or review approvals. This helps maintain code integrity, increase transparency, and improve #collaboration among #developers and #teams.
